Process Isolation and Syscall Monitoring with eBPF
Docker containers are widely used in modern software development for their lightweight, portable, and scalable nature. However, due to their very nature of sharing the host kernel, they enforce a strict level of process isolation to prevent interference between containers. In this post, I’ll demonstrate how you can distinguish kernel system calls made by processes within a container using eBPF (extended Berkeley Packet Filter) programs.
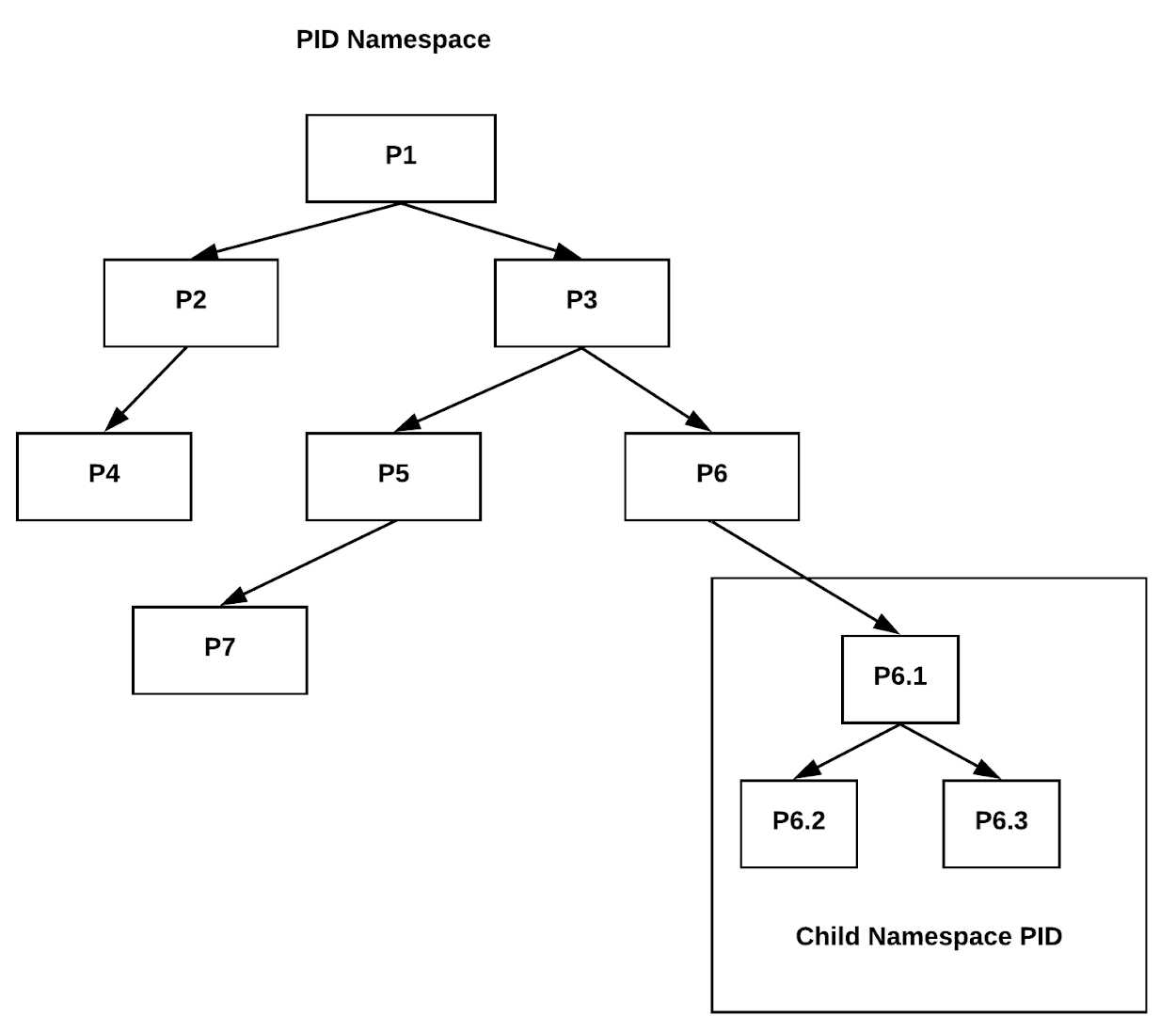
PID Isolation in Containers
PID namespaces are integral to Linux kernel namespaces, designed to provide each group of processes with a unique set of process IDs. This allows processes within a container to function in a separate, isolated environment. The segregation achieved by PID namespaces enhances process management and resource allocation by limiting interactions between processes. This feature is critical in container technologies like Docker and Kubernetes for maintaining process isolation.
Determining PID Mapping in Docker Containers
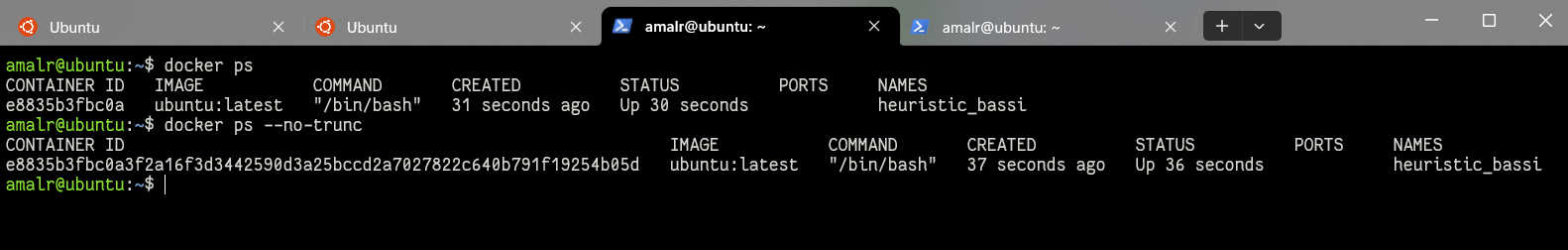
To identify process ID (PID) mapping within Docker containers, follow these steps:
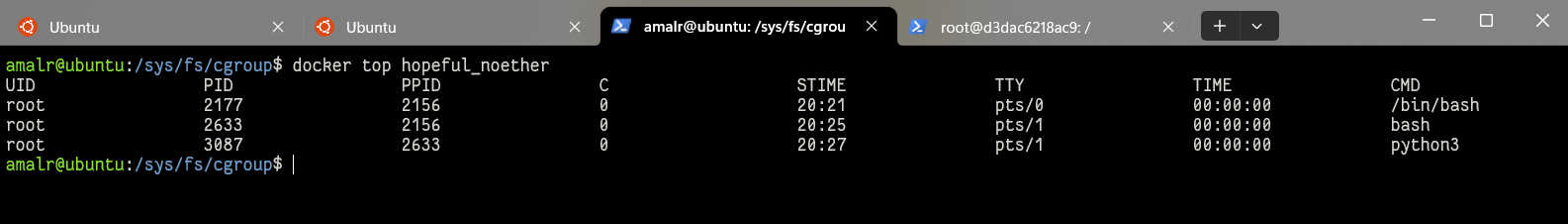
If the above step is insufficient, navigate to the directory /sys/fs/cgroup/unified/docker/<long-image-id>/cgroup.procs to view PPIDs. A simple shell command can then be executed to map these PIDs.
Using BCC Tools with PID Parameters
The BPF Compiler Collection (BCC) is a toolkit for developing and executing eBPF (extended Berkeley Packet Filter) programs. BCC provides a variety of pre-built eBPF programs and libraries suitable for system performance monitoring, syscall tracing, and more. BCC tools commonly support the -p flag, allowing users to specify a PID for targeted monitoring. These tools are instrumental in gaining insights into system operations and enhancing security measures within containerized environments.
Bonus
If you’re facing trouble setting up BCC tools on your system, consider using my Docker image with pre-installed BCC tools. This image is designed to simplify the process of monitoring syscalls within Docker containers.
Make sure to launch it with
1
docker run -it -d --privileged -v /lib/modules:/lib/modules -v /sys:/sys -v /usr/src:/usr/src amalrajan/ubuntu-bcc:focal
This command initiates a detached container with privileged access, necessary for syscall monitoring, and mounts the required directories to ensure the container has access to the host’s kernel modules and source directories.